Trust and the Issues with context
Trust is important! It provides mechanisms in public key infrastructure (PKI) that keep our (digital) world turning.
Windows and Linux follow different approaches. Both have their issues…
The Windows world of trust
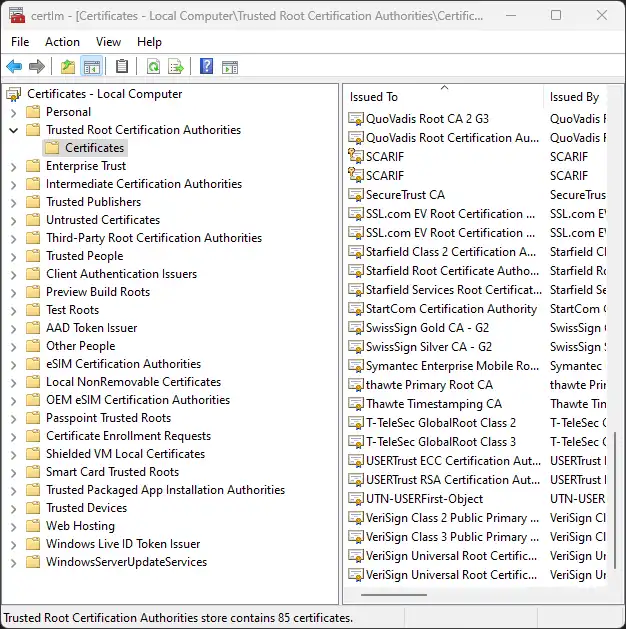
Microsoft Windows has the Windows Certificate Store. One for the
Machine (certlm.msc), providing the baseline, and another one for the
User context (certmgr.msc).
There are attempts to separate certain types of certificates by their
intent e.g. Trusted People for S/MIME signatures and encryption vs.
Trusted Publishers for driver signatures.
The stores reside in the registry while some data is stored on the hard disk. Central management, in terms of publication of certificates, through Active Directory is possible.
It is great to have one place to maintain trust. But why do I have the same roots of trust for e-mails and websites?
If I put a Root CA certificate into the Trusted Root Certificate Authorities, I can verify an e-mail signature created with a leaf certificate coming, but also approve that this certificate can issue a TLS certificate for instance for my mail provider - Add some DNS spoofing and all data is breached.
I may want to verify the signature on an e-mail sent by a government institution (think of the NSA), but I don’t want them to be able to play Man-in-the-Middle when browsing the web.
As a side note, there is something in windows called crypto provider, which allows engines or hardware to be called. This is quite nice for the fact that is often faster that PKCS#11.
The Lunix world of trust
In Linux there is no store. A trust is established by referencing/importing
a PEM-file containing one or more certificates. This happens for instance
in Node.js by declaring the environment variable NODE_EXTRA_CA_CERTS and
set its value to a path to the PEM-file or Python Requests with the
environment variable REQUESTS_CA_BUNDLE. From the Python’s variable name
it is assumable that there is context involved. It is just for the HTTP(s)
requests made using the Requests library.
You program n email client? Go imagine yourself a pace where to store a
PEM-file, take care of yourself to load it, manage it, maintain it, and
especially use it correctly when validating signatures.
I want to be able to fine grain my trust for certain contexts, but I don’t want to reinvent the wheel as there are a limited set of contexts.
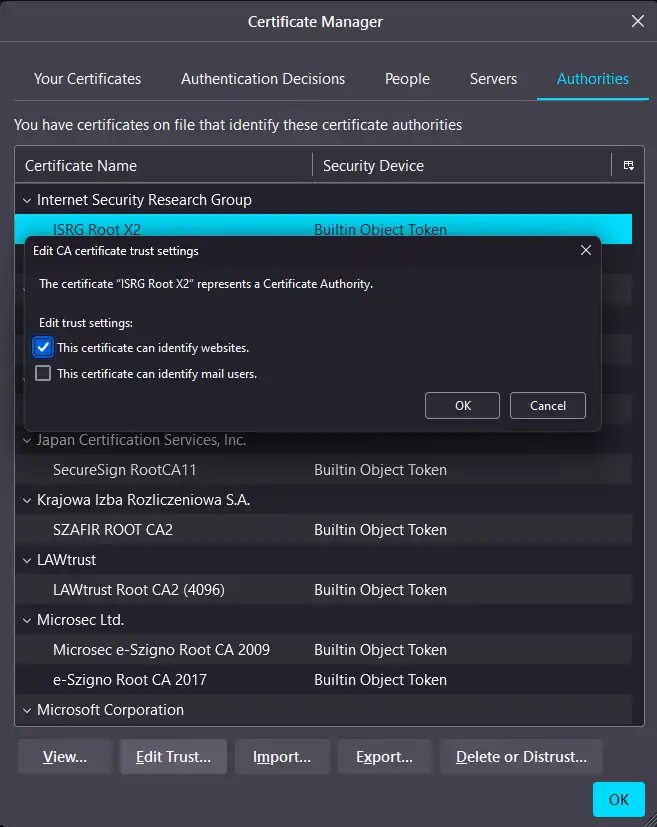
The Mozilla world of trust
Mozilla, with its browser Firefox and the e-mail client Thunderbird, has come to the same conclusion. In their store you can select the context of trust.
From a management perspective the dialog is a nightmare. No search, nor overview what trust is anchored on which certificate and so on. Beside that there is no link between Firefox and Thunderbird.
The European Union and the Qualified Website Authentication Certificates (QWAC) of EiDAS 2
The same issue arises with the latest attempt of the european union, and the issuance of Qualified Website Authentication Certificates (QWAC).
Politicians in the European Union seem to not understand what huge security risks arise from just putting some certs into the root store. Especially with fully fledged surveillance capitalism in place, EU members governments eavesdropping oppositions and journalists, far-right parties in cabinets and governance as well as the general rise of fascism.
Summary
I pretty sure we can and should do better.